
Institution of Electronics and Telecommunication EngineersÉCRIRE
Our Sponsors



© 2021 IETE BITS

Artificial intelligence (AI) refers to the simulation of human intelligence in machines that are programmed to think like humans and mimic their actions. The term may also be applied to any machine that exhibits traits associated with a human mind such as learning and problem-solving.

Over the past few decades, a lot of research and advancement has been going on how to increase the speed of processing of data and its storage.

Cyber security is the way of practice of protecting systems, networks and programs from digital attacks. Cyber-attacks are generally focussed on changing, accessing or destroying useful information; extracting money from users by unfair means; or interrupting the procedure of normal businesses.

DDoS attacks are a primary concern in Internet security today. Explore details about how DDoS attacks function, and how they can be stopped.
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
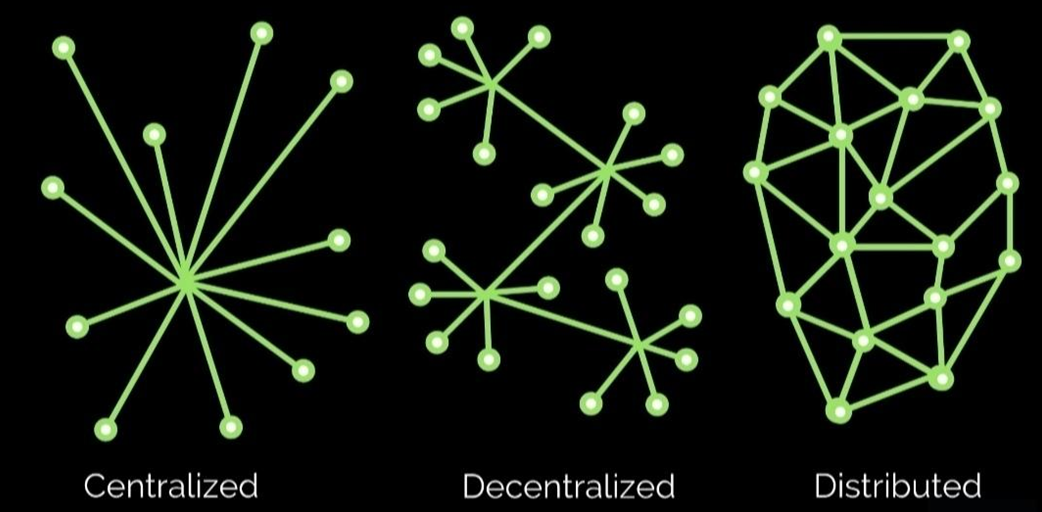
Decentralization is the process of making system where no single entity is able to own the master key and govern the data and overall system; even they created the system. It is a powerful word in today’s society and another feature of Blockchain that makes people hopeful about the future where every individual will have control and power over the internet.

The UNREMOVABLE FOOTPRINTS INTRODUCTION Do you know what footprints of you are unremovable? No idea? Think again for some times. Again no idea? Ok , let me give you one clue, and clue is that this is a technical blog. Wait! wait! Are you thinking that this blog is not for you, because you aren’t a technical guy? If your answer is ‘yes’ then believe me this blog is going to be very important for you.

In today’s time, the internet and computers are being used in every field and all our work is done through the internet whether it is a government or private work. So this means all kinds of data are being exchanged in some way. The way the internet is being used all over the world millions of users use it every day. So it is very important that user’s security should also be noted on the internet because every day on the internet there is news of people becoming the victim of fraud, hacking. Therefore it becomes necessary to provide security to secure the data of users from cybercrime, cyberattack and to avoid cybercrime, cyberattack, cybersecurity is being used.

Out of beginning with the Era- of - Barter System towards growing Digitally we accomplish a virtual asset as a medium of exchange baptized as – CRYPTOCURRENCY. Out of it individual coin ownership records are stored in a ledger existing in a form of computerized database using strong cryptography to secure transaction records, to control the creation of additional coins, and to verify the transfer of coin ownership.

On Sunday night when I was having a movie night with my family, I was watching the movie Mission Mangal first time after it releases, which is an inspirational story of a group of scientists who work relentlessly to make the Mars Orbiter Mission successful.

As we know that in today’s world, Technology is increasing at a rapid rate. Automation and Artificial Intelligence will soon be prominent. Because of these unemployment is growing at a rapid rate.